How to protect your backup folder from CryptoLocker and other ransomware in an Active Directory Domain Services
We are going to show how to create a secure folder that only the domain administrator and the backup user will be able to access.
The backup user must be used uniquely by Uranium Backup, it’s a service account not intended to be used to work on the client machines. Then we’ll configure Uranium Backup to make it able to access the folder without sharing the access credentials with the local machine or the local user.
This backup strategy won’t let a machine infected by CryptoLocker or other ransomware to access the backed up data, making you able to restore it in case of disaster. Remember that the backup integrity must always be checked, accordingly with the backup cadence and the data retention policies.
Also note that if Cryptolocker or other ransomware infect a machine used by the domain administrator, gaining the maximum privileges, it will be able to access the secure folder.
Follow the guide
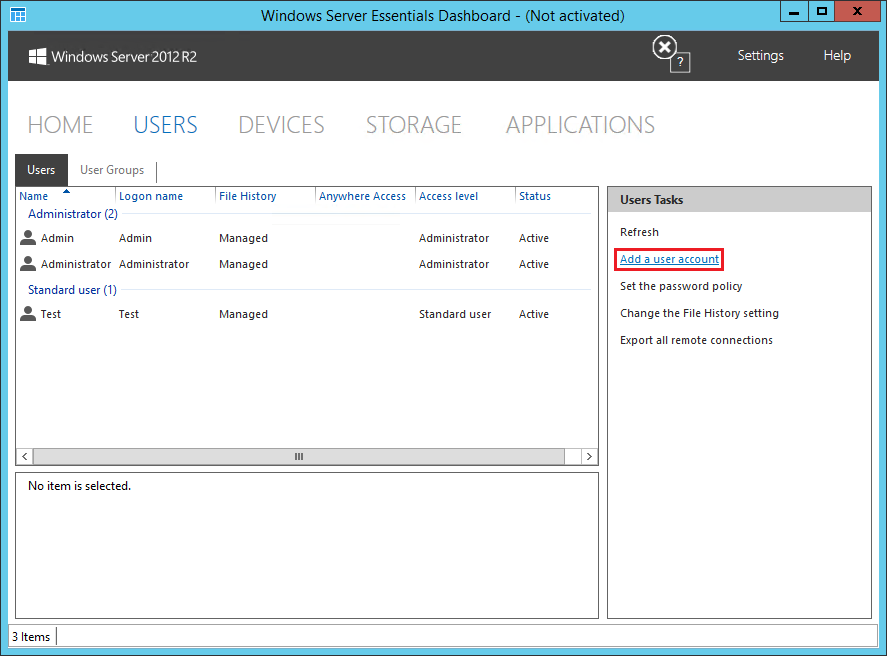
The first step is to create the backup user
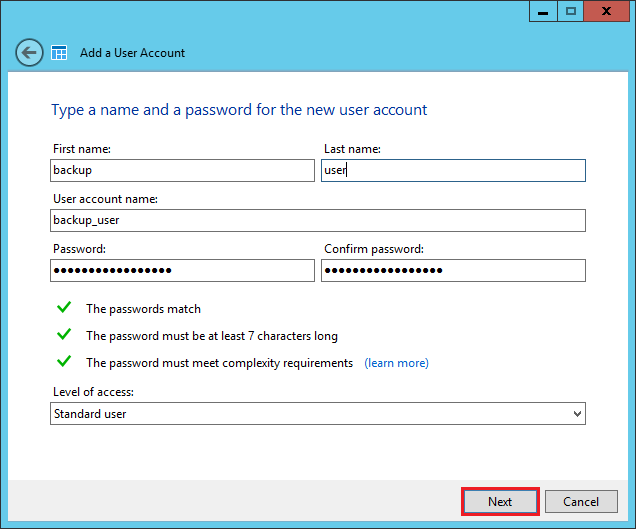
Then create the backup folder. In our example we used a Windows-based file server but it’s possible to use a Linux-based NAS without changing the backup strategy
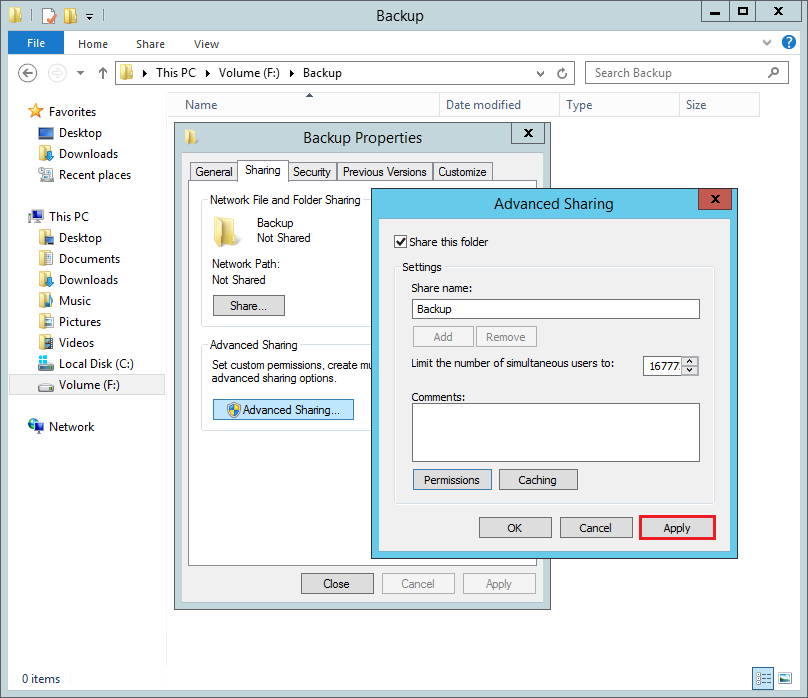
Share the folder
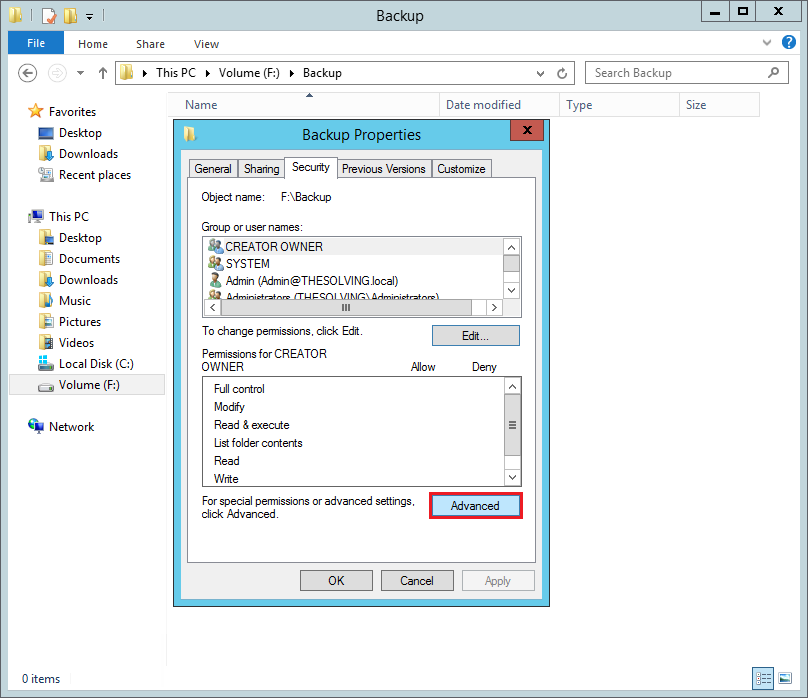
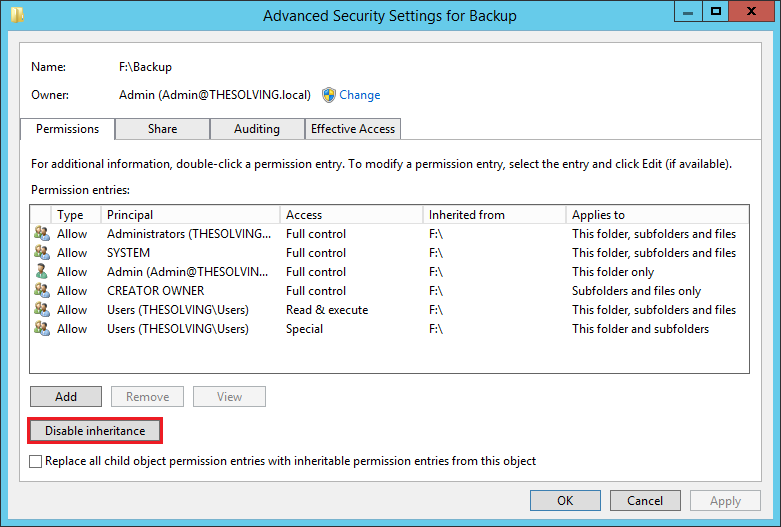
Then open the Advanced settings of the Security tab
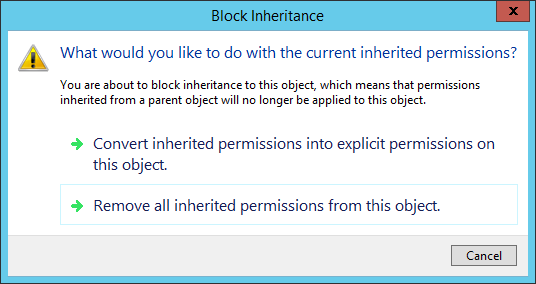
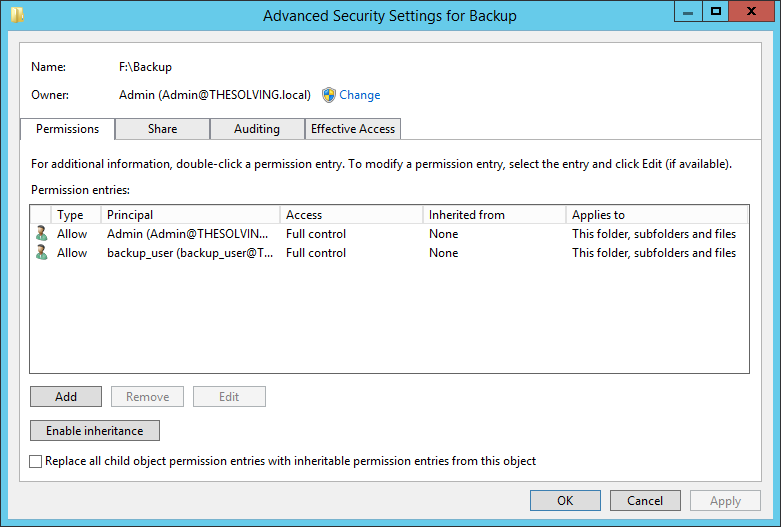
Disable the permissions inheritance
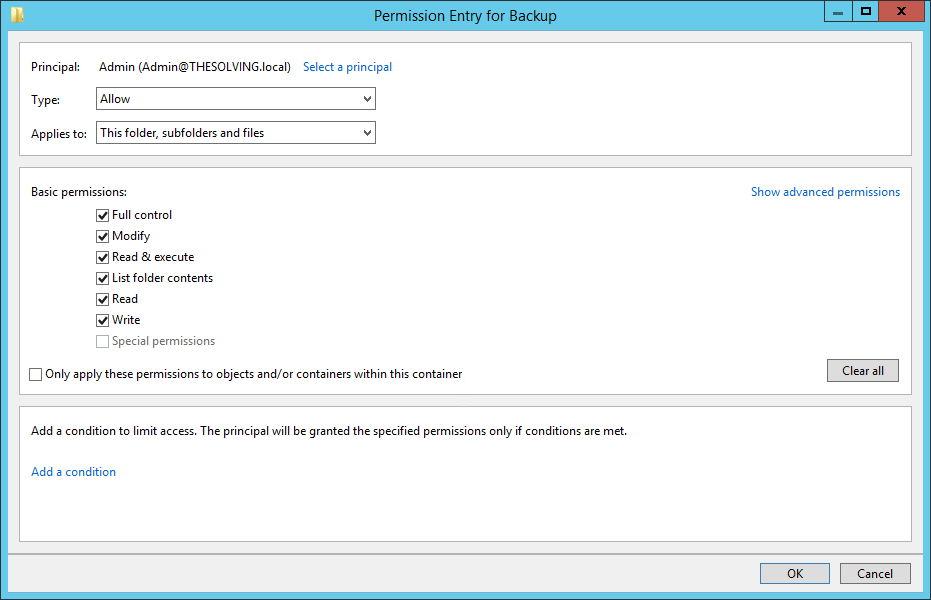
The permissions entry box will be empty. Add a new permission Entry to allow Full Control to the domain administrator
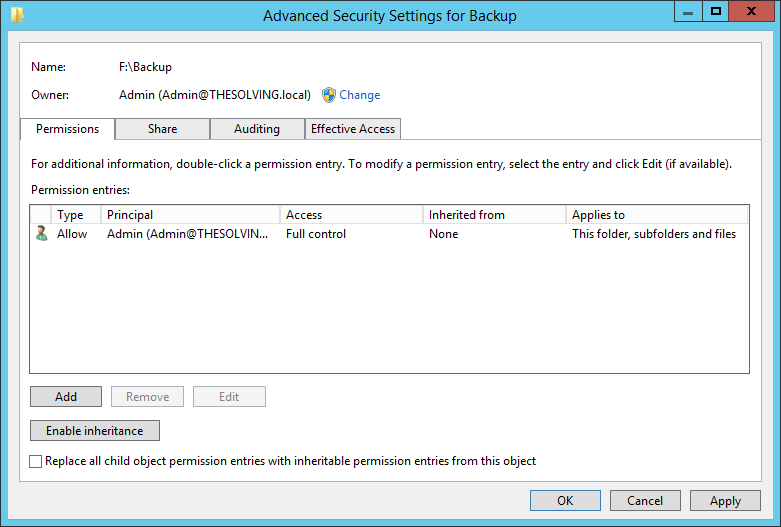
Then allow Full Control to the backup user
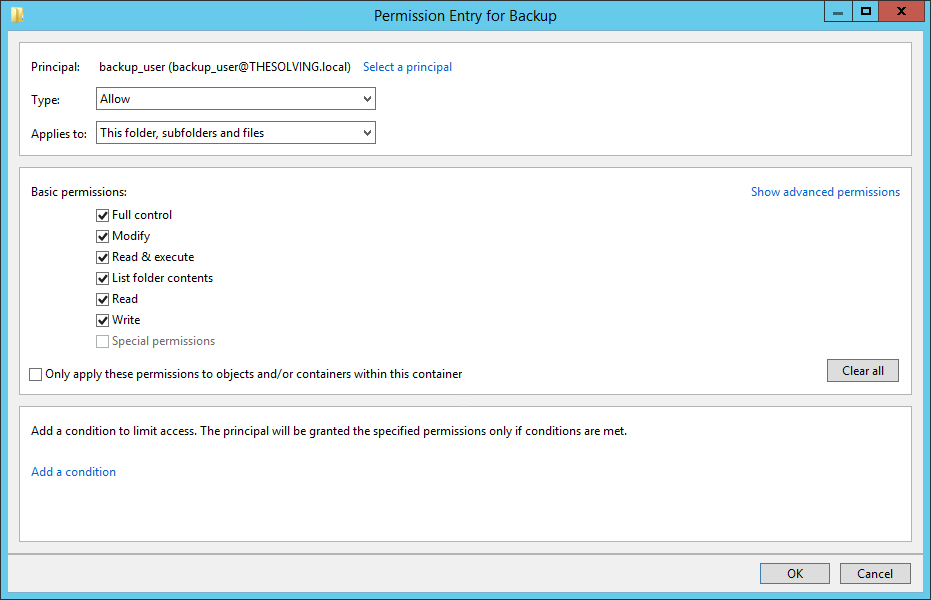
The backup destination is ready. Now open Uranium Backup and install the service specifying the backup user as the service account
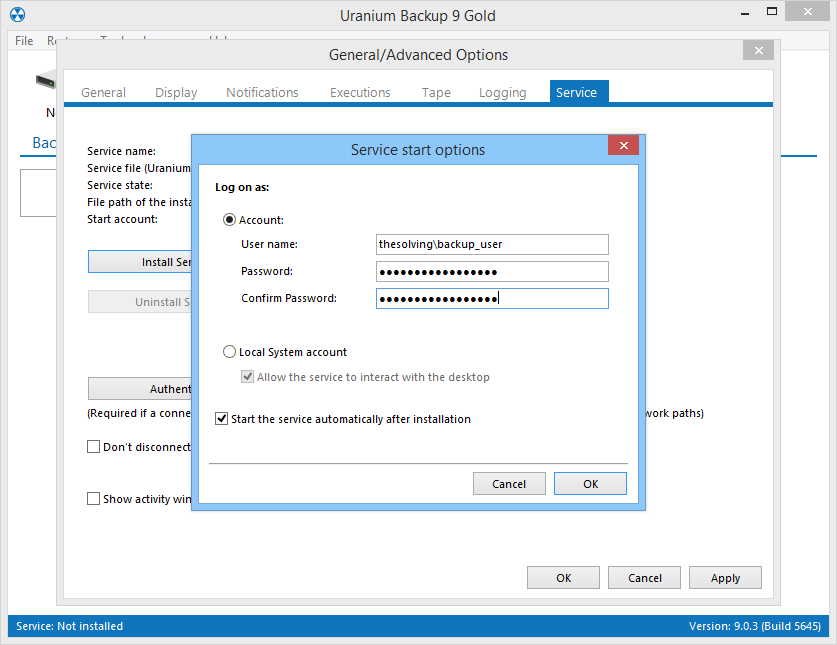
Note: you must allow the backup user to access the folders containing the data you need to back up. The backup user access credentials must never be specified as the access credentials of Uranium Backup element or destination paths. As only the service is configured to run under the backup user, only the scheduled backup will be able to access the secure folder. Any manual execution will fail to access the folder.

 Français
Français
 Deutsch
Deutsch
 Italiano
Italiano
 Português
Português
 Español
Español